
On 14th December, the cryptocurrency community witnessed a security breach involving Ledger’s Web3 Connector library, known as the Ledger Connect Kit. This library is used by dApps and other applications made by other companies and projects to interact and connect with the Ledger hardware wallets using Ledger Extension or Ledger Live.
The Ledger Connect Kit Loader, which is also a package, allows dApps to load the latest version of Connect Kit at runtime from a CDN so that they can improve the logic and UI without users having to wait for wallet libraries and dApps updating package versions and releasing new builds.
The Ledger Connect Kit was exploited by malicious actors who compromised Ledger’s NPMJS repository of the same by introducing a dangerous drainer script that enabled the hackers to trick the users into authorizing malicious transfer of their funds to the hackers, in other words, the users were phished.
The Exploit Unveiled
Allegedly, a malicious version of the Ledger Connect Kit package was published on Ledger’s NPM repository by a malicious advisory or the hacker using an ex-Ledger employees account, who fell victim to a phishing attack.
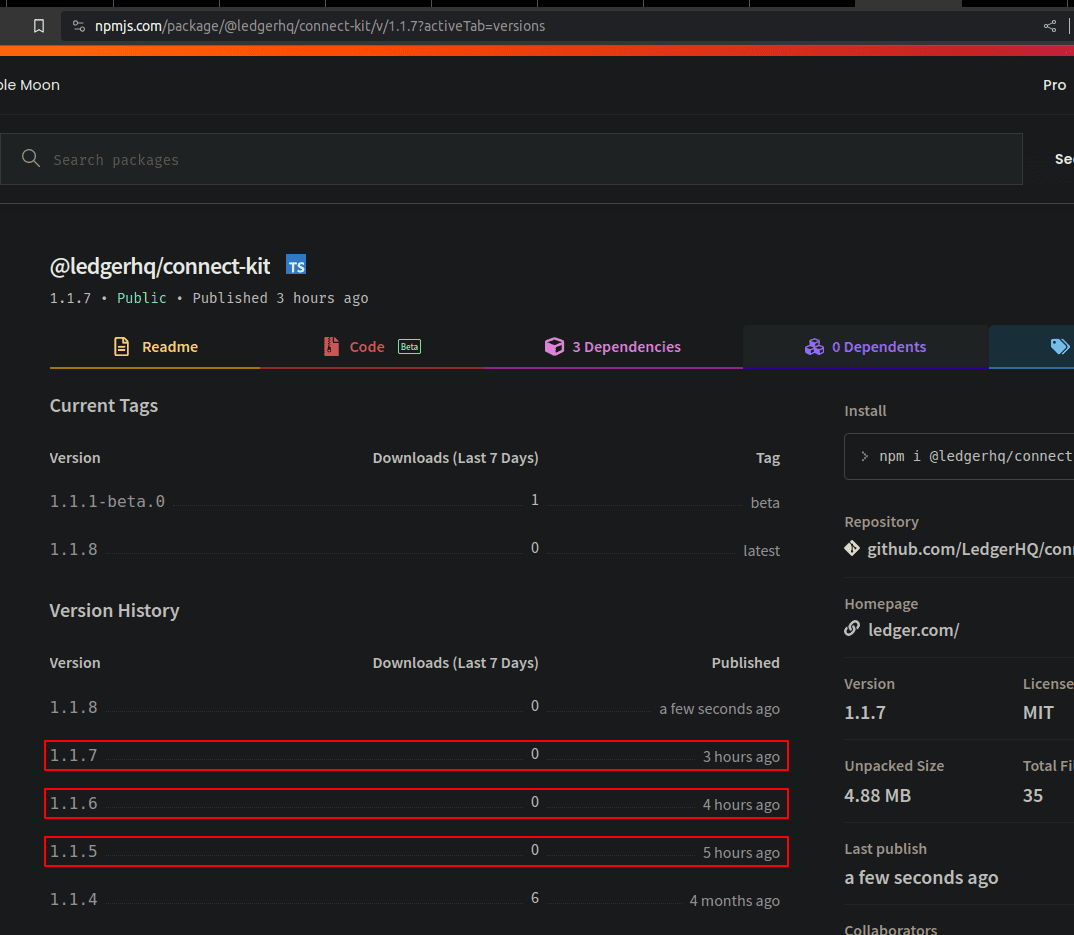
In short, Ledger’s control of the NPM repository package was accessed in an unauthorized manner. What ensued was a threefold release of compromised versions of the connect-kit package on the NPM repository, each concealing malicious code. Which now seems to be removed.
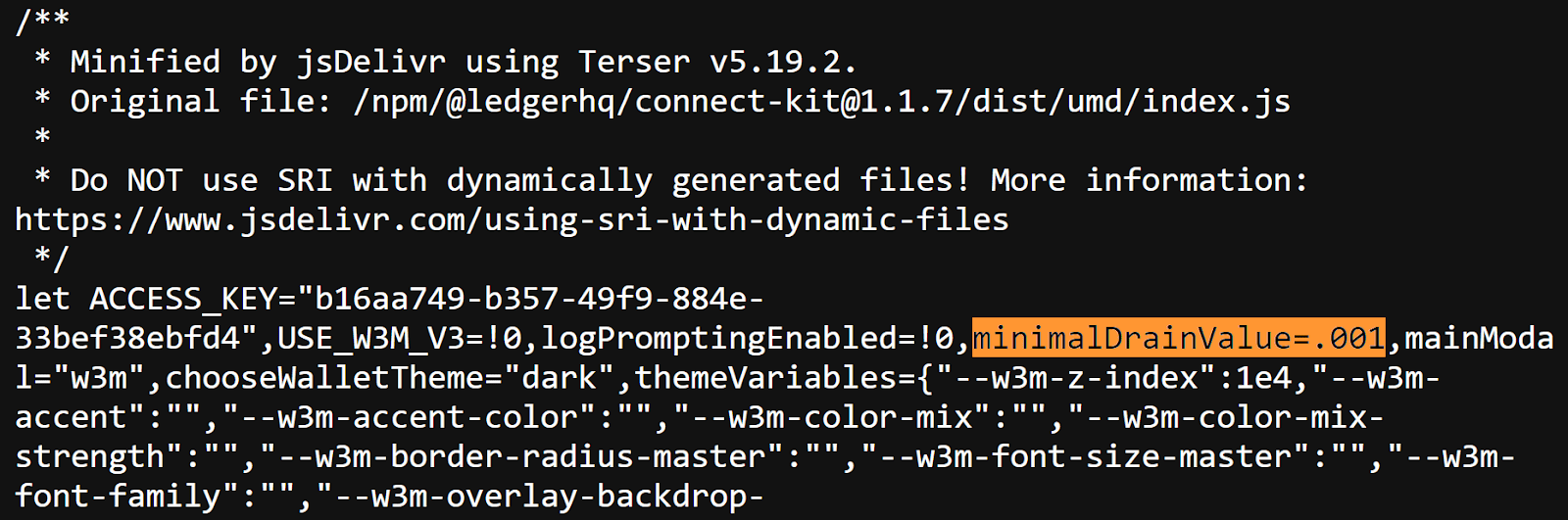
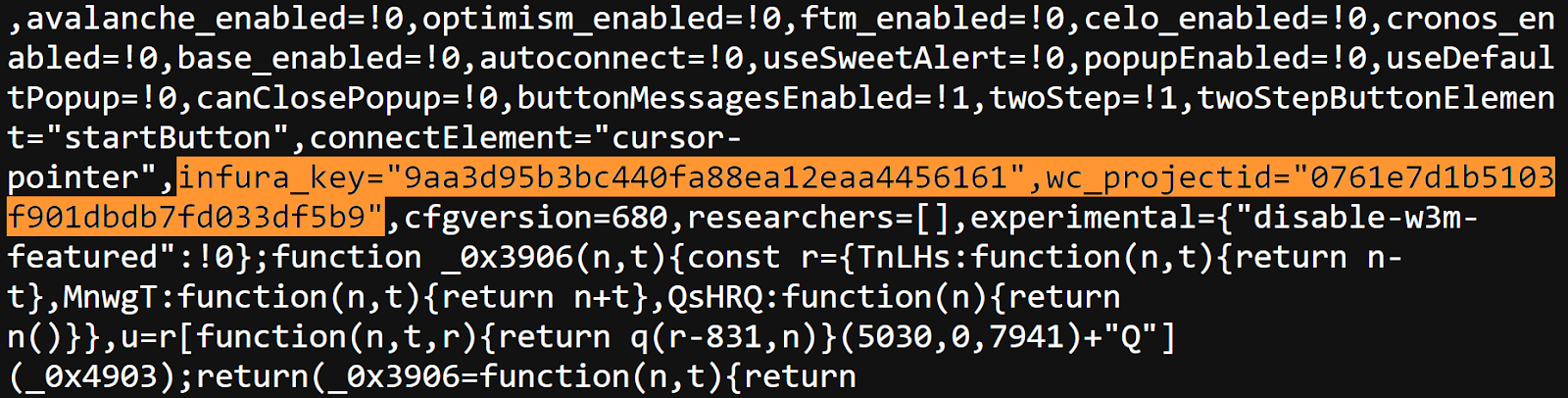
The hacker added a malicious drainer script to drain the users coins when they connect their Ledger wallet to the dApps that uses this compromised library. According to the Ledger Chairman and CEO, Pascal Gauthier, this was accomplished by the malicious code by using a rogue WalletConnect project to reroute funds to a hackers wallet.
A “drainer” is a malicious code meant to trick the users into moving funds from their wallet to the hackers wallet. In this situation, it seems that the compromised Ledger library contained code that triggered unauthorized transactions, depleting cryptocurrencies from the wallets connected to those dApps.
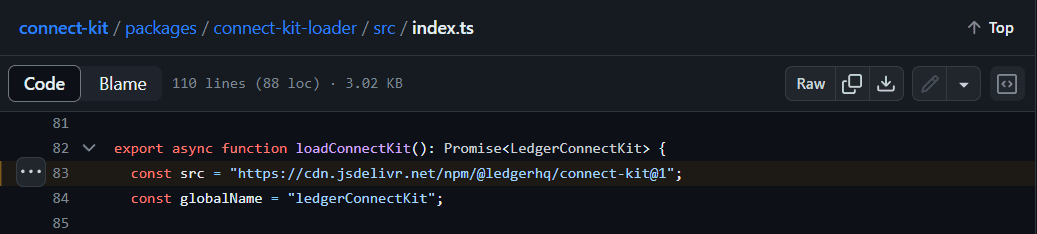
The Ledger connect-kit-loader also seemed vulnerable. As shown below, it is meant to download the latest version of connect-kit
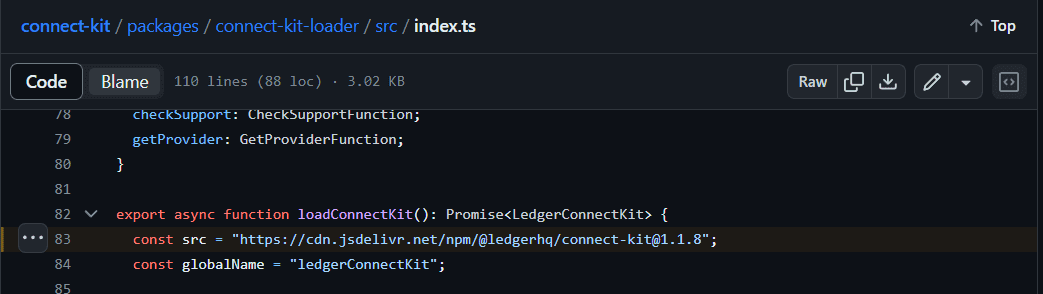
This approach has provided attackers with an avenue to infiltrate numerous libraries by compromising the connect-kit alone. Notably, the last verified version from Ledger is 1.1.4, yet three subsequent releases up to 1.1.7 were posted on the day of the incident, all deemed compromised.
This approach has provided attackers with an avenue to infiltrate numerous libraries by compromising the connect-kit alone. Notably, the last verified version from Ledger is 1.1.4, yet three subsequent releases up to 1.1.7 were posted on the day of the incident, all deemed compromised.
This has now been fixed, as you can see below the loader will download the version specific package, that is version 1.1.8.
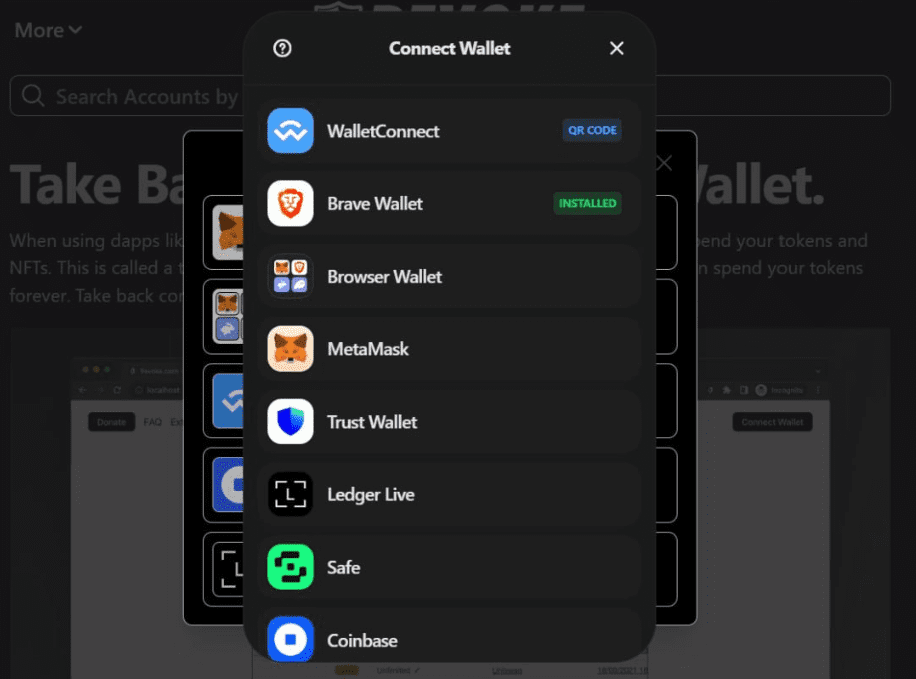
This below image shows you what the hacked version looked like. What’s clearly visible is an additional modal overlaying the original one. Upon connecting your wallet to this malicious modal and confirming a transaction or message, your funds will get drained.
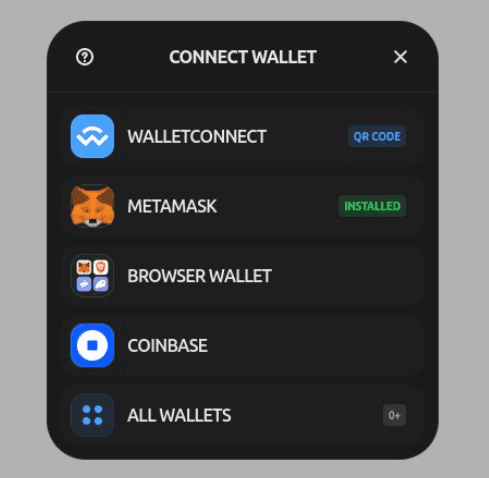
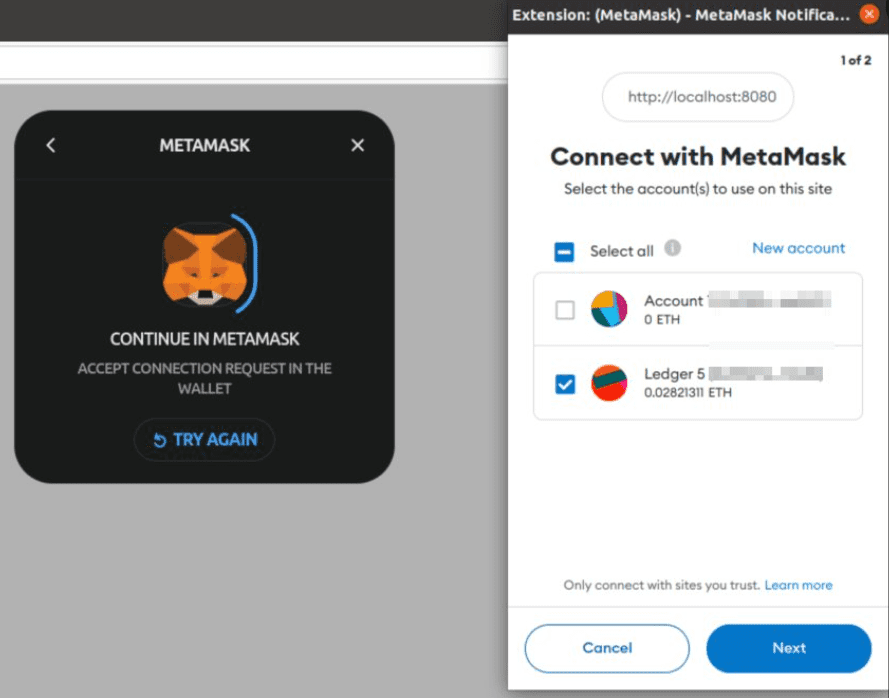
The app’s behavior, affected by the malicious code, unfolds as follows: The dApp loads and promptly presents a modal to connect the wallet with. After the customary wallet connection, the user is asked to confirm a transaction labeled “claim”. Upon user confirmation, funds are swiftly depleted.
Many popular dApps rely on this package for integration with Ledger hardware wallets. Consequently, anyone dependent on Ledger’s Connect Kit experienced the impact. This includes well-known bridges, and dApps such as Pancakeswap, SushiSwap, Zapper, Phantom, Balancer, Revoke.cash and OffchainLabs/arbitrum-token-bridge.
While these are a few mentioned, it’s also crucial to recognize the domino effect within the web3 landscape. Given the intricate chain of dependencies, incidents like these have an indirect impact, reaching far beyond what may initially meet the eye.
Swift Action and Remediation
To address the exploit, Ledger swiftly responded by removing the malicious file within 40 minutes of discovery, and the incident lasted for less than two hours. While the malicious file remained live for approximately five hours, Ledger spokesperson Phillip Costigan clarified that the specific window for fund drainage was confined to less than two hours.
Ledger promptly released a genuine and clean version of the package, that is version 1.1.8, of the connect-kit. Users are advised to update to this latest version, as it is deemed safe for use.
Quantifying the Toll
In terms of financial impact, this incident has potentially resulted in a loss of approximately $600,000 from Ethereum accounts. Ledger, in collaboration with WalletConnect and their partners, reported the wallet address associated with the hacker. Tether has taken decisive action by freezing the USDT linked to this malicious actor. For further details, you can refer to the adversary’s address.
The Ethereum account linked to the incident has been flagged on Etherscan for heightened scrutiny.
Security Implications and User Vigilance - The importance of choosing the right wallet
Emphasizing the critical role of selecting an appropriate wallet, it is strongly recommended to opt for a hardware wallet. It’s always better to use a hardware wallet to eliminate the exposure of your private keys to the internet for signing transactions. It is crucial to use the right hardware wallet to mitigate attacks like this and keep your funds safe.
It is so important for a hardware wallet to have a display for showing all the necessary transaction information to the user for manual visual verification. Another important factor is that the wallet should support default clear signing. This means that the HD wallet should parse the transaction details into human readable form, that is the user should be forced to use any software in the middle. The wallet should be able to show you the necessary details such as the type of coin, amount of coin and the address you’re sending your coin to on a large enough display for you to visually verify before confirming and signing the transaction.
The aforementioned event wouldn’t have occurred if the users wouldn’t have blind signed the transactions. While Ledger wallets support clear signing for the apps that can be downloaded and installed through Ledger Live (Bitcoin, Ethereum, Solana etc.). When it comes to DeFi, Ledger wallets do not support or offer clear signing on default and the users are forced to trust the smart contracts. Users are forced to enable blind signing for signing transactions on DeFi, dApps. The screen on the Ledger wallets are also too small to display smart contract details anyway. The users should only trust what is shown on the hardware wallets display and not on the host system. This is the same reason why using wallets like Tangem that do not have a display is also a bad idea.

Another very important thing while choosing a hardware wallet is that it should be open source and reproducible. This is crucial because there is a very important computation that happens inside the hardware wallet that handles or uses sensitive information and elements like your private keys. The transaction signing function is the most important function written in the software. Hardware wallets like Ledger are closed source and no one can verify and confirm what is running on the device.
If something like this exploit can happen, that is a former employee’s account being used by a hacker to push malicious code to a library used by thousands of dApps and then publishing it in an unauthorized way to drain user funds. Imagine someone inside or outside Ledger, gaining access to the Ledger wallets firmware repo and making a change to a single line of code in the ECDSA function which is the transaction signing function and Ledger pushes a firmware update. This would be enough to expose all of the Ledger users private keys and enough for the hacker to steal all of the crypto secured by Ledger wallets.
Security Implications and User Vigilance - Why self custody is important
It is always advised to self custody your funds as it will give you complete control, access and ability to manage them however you want whenever you want. Staying far away from crypto exchanges and hot wallets will reduce the attack surface drastically hence improving your crypto security.
However, from the recent incident it’s clear that even after adopting self custody users still have to be alert and vigilant in the field of web3 and crypto. It is important to verify your transactions on screen with your hardware wallet while interacting with DeFi apps or dApps. Opting for a bitcoin only wallet, using multi-sig and switching to an air gapped design won’t solve this issue.
The key is for users to properly verify transactions on their hardware wallet screen and not blind sign, encouraging security reviews and disclosures, and open sourcing everything. By choosing the right hardware wallet that has a display, that supports clear signing and is open source, you would be making self custody easier hence securing your crypto funds.
Authors
Sreehari B, Cryptography Research Intern
Irshad Ansari, Full Stack Developer
Ujjwal Kumar, Software Engineer
Connect with us:
Twitter :twitter.com/CypherockWallet
Telegram: t.me/cypherock
